Broadsign Control Administrator offers the possibility to search audit logs (also called audit trail) for user activity that is logged by Broadsign Server.
Note: You can only access this feature if you have enabled Broadsign Control Live on your domain. For more information, contact your Sales representative or Broadsign Services.
Note: Audit logs must be activated in your Broadsign Direct domain. Contact Broadsign Services to activate the logs.
Broadsign Server logs all user activity, including: operation type, operation performed, user id and timestamp.
Broadsign Server does not save logs automatically for all users. It is a domain setting and you must contact Broadsign Services to enable users. From the moment the option is activated, allow up to 15 minutes for operations to start being logged.
The audit logs can be searched in-product by user name, operation type and log message contents.
Audit logs are captured by the application servers for both API users and Broadsign Control Administrator users. They are recorded asynchronously.
Audit logs are also captured for operations made in Broadsign Direct.
Note: 60 to 90 seconds are required for an operation to be sent to the audit log and be retrievable via the Broadsign Control Administrator search.
Broadsign keeps audit logs indefinitely, so we can provide log files from any date.
To access audit logs, users need the audit_log privilege. For more information, see Privileges Tab.
The following video outlines how to use the Audit Log feature:
Audit Trail
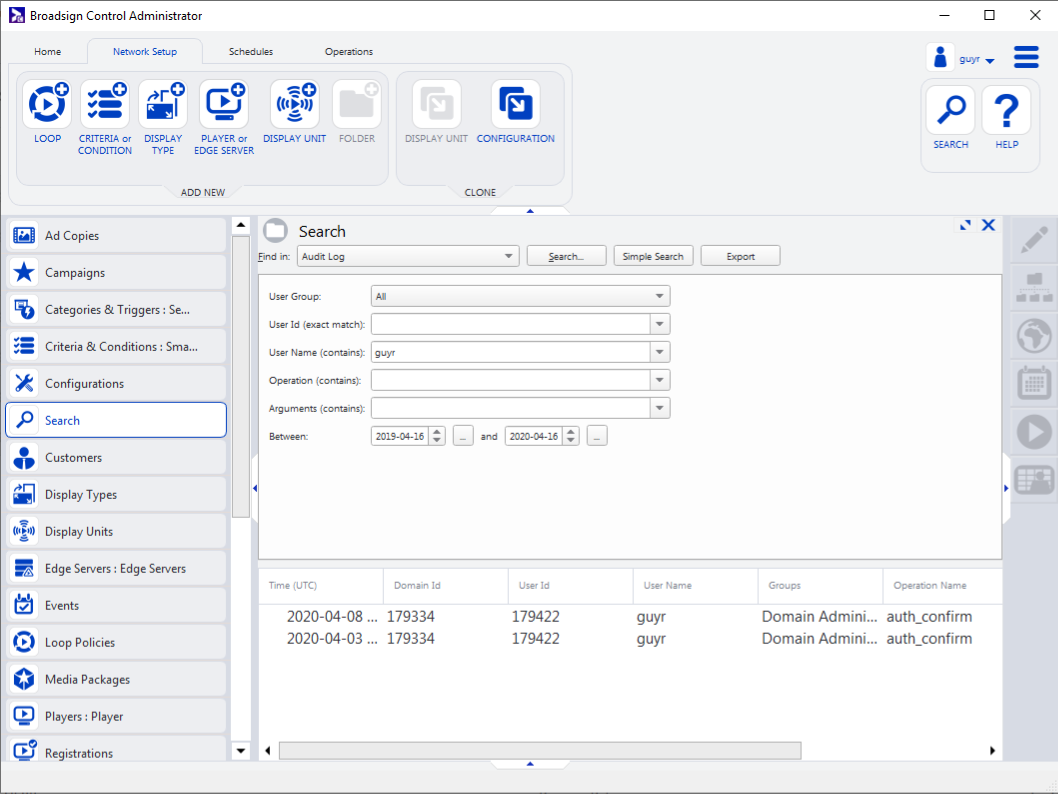
Audit logs can be generated via the Search function.
To generate audit logs:
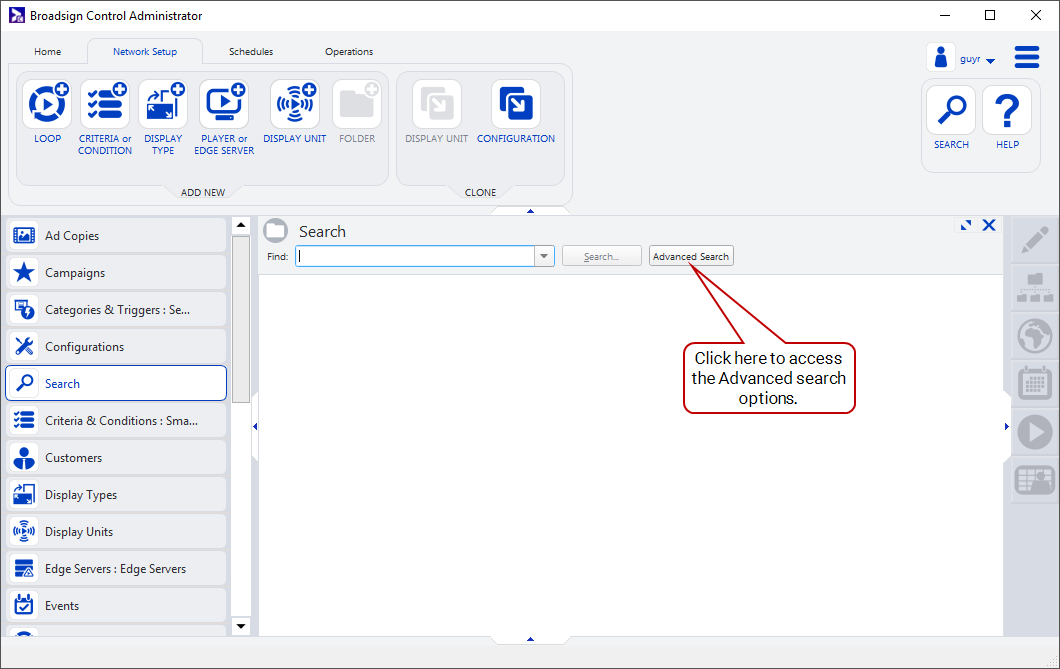
- Click the magnifying glass icon at the top-right of Broadsign Control Administrator.
- Click the Advanced button to access the Advanced search mode.
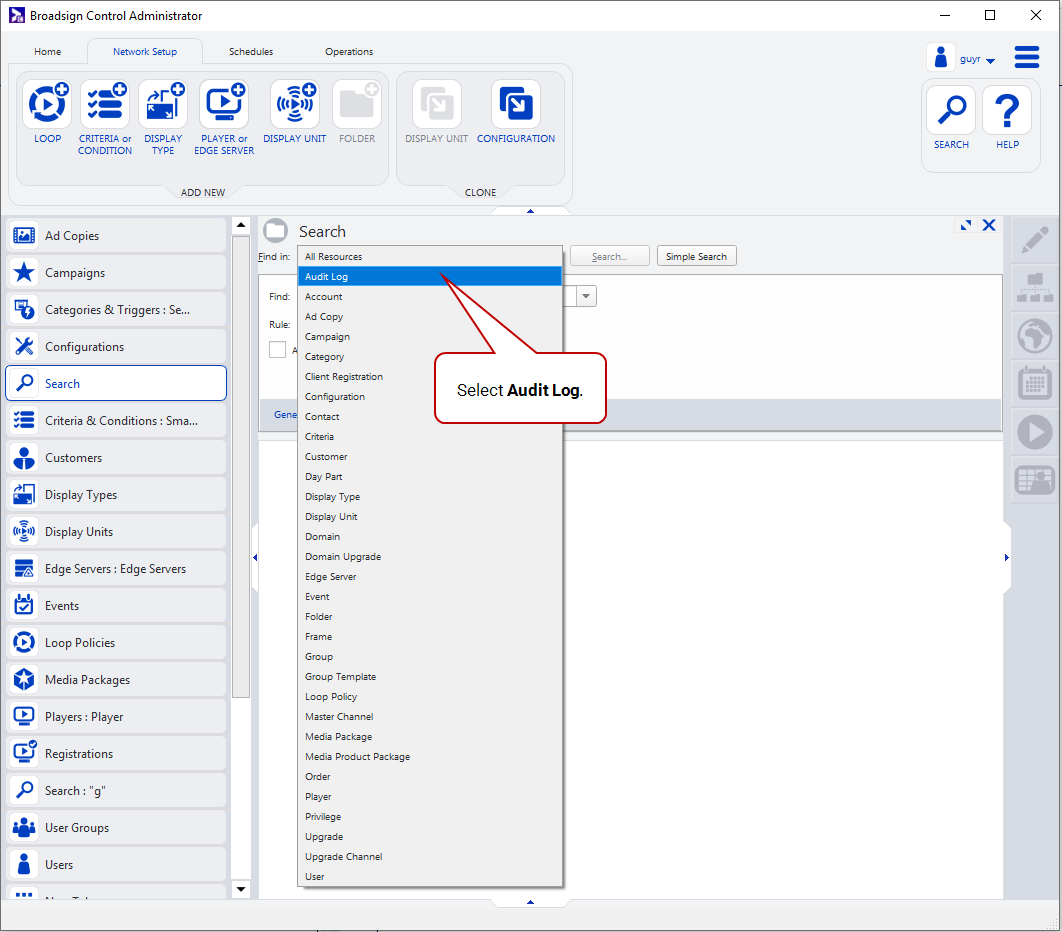
- In the Find field, select the Audit Log resource.
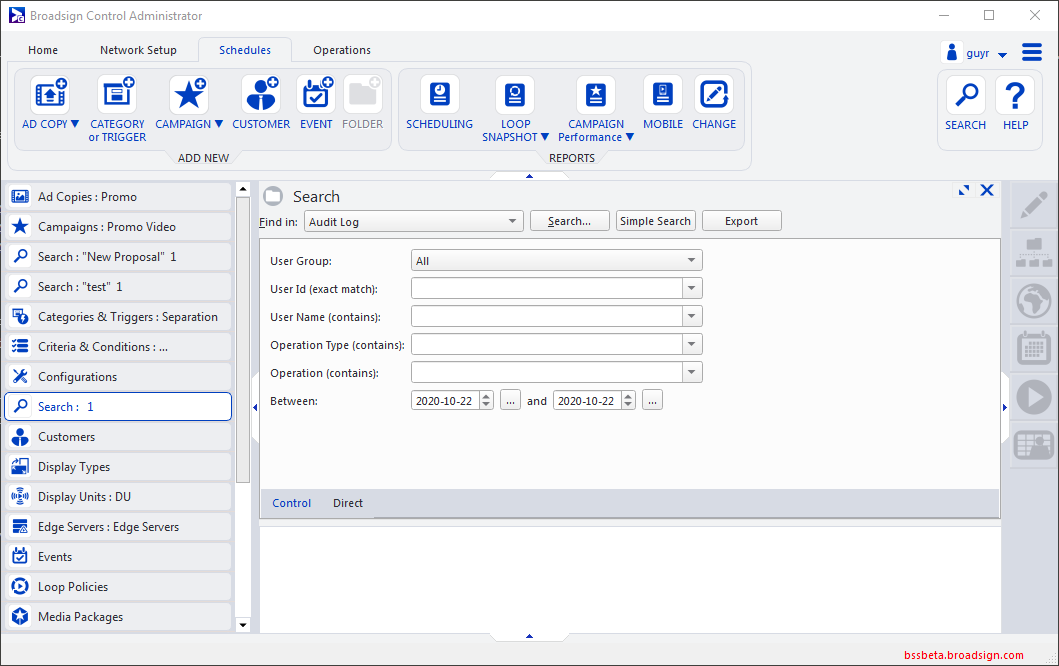
- Select whether you want to perform an Audit Log search in the Broadsign Control or Broadsign Direct user activity by selecting the Control or Direct tab at the bottom of the Audit Log search options window.
- Select in which User Group you want to perform an Audit Log search.
- Enter a query in one or more of the query fields.
- All
- Sales
- Manager
- Admin
- Sales Operator
- Select a Start Date and End Date for your query. This is mandatory.
- Click Search.
The Audit Log search options are displayed.
The drop-down menu lists all the groups that are activated on your domain.
Searching audit trail log by user group implies searching on all users in a specific user group.
If a user is a member of a given group at any time within the start/end date range, that user’s actions are included in the query results. For example, user Bob belongs to group A from Jan. 1 to 7; group B from Jan. 8 to 10, and groups A and C from Jan. 10 onwards. If the audit trail query is performed on Jan. 31, searching by user group for group B, operations performed between Jan 8 and 10 are returned.
| Query Field | Description |
| Role |
When performing Broadsign Direct searches, the following Roles are available: |
| User Group | When performing Broadsign Control searches, queries audit trail log in specific user groups. |
| Email (contains) | When performing Broadsign Direct searches, queries audit log for an email address and finds logs that contain the string. |
|
User id (exact match) |
Searches audit trail log for a specific user. |
|
Username (contains) |
Searches audit trail log for a user name and finds logs that contain the string. |
| Operation Type (contains) | Searches audit trail log for an operation type and finds logs that contain this type, for example, "content_mgr_update". See Operation Types. |
|
Operation (contains) |
Searches audit trail log for an operation and finds logs that contain the string within the actual body. For example, "{\"domain_id\":123,\"active\",}. |
All queries are scoped to a maximum time period to limit the size of the data scanned in each query.
The search results are displayed in the Search results section.
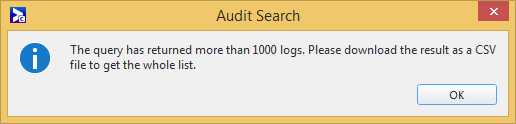
If your search result has more than 1000 logs, the 1000 most recent logs are displayed in the Search result area. You will be prompted to export the results to a .csv file to see all the logs.
The audit log results can be exported to .csv for offline analysis by clicking the Export button. If your search result has more than 1000 logs, then it will not be displayed in the Search result area and you will need to export it to a .csv file.
Your system downloads a .csv file with the audit logs result. The file uses UTF-8 encoding. The file name is in this format: AL_[year].[month].[day].[hour].[minute].[seconds]. For example: AL_2020.04.16.13.48.13.
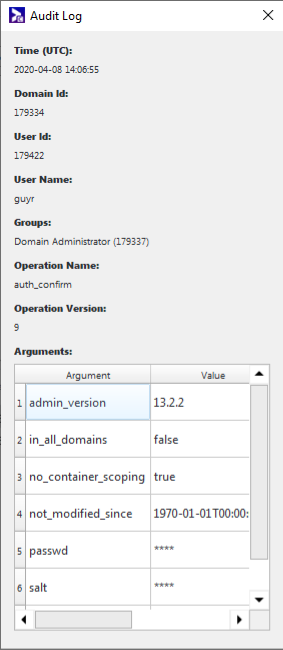
The search results that are displayed in the Search results section contain the following information (columns):
| Column | Description |
| Time (UTC) | Date and time at which the operation was logged, in UTC. |
| Domain ID | Domain ID of the User doing the operation. |
| User ID | ID of the User performing the operation. |
| User Name | Username of the User performing the operation. |
| Groups | List of the Groups to which the User doing the operation belongs at the time of the operation. Each group is represented by its ID and its name. |
| Operation Name | Name of the operation being logged. In most circumstances, it will have the format {resource_type}_mgr_{action}. |
| Operation Version | Version of the operation being logged. |
| Arguments | Arguments used in the operation. |
You can move the columns around and sort by each column. You can also add or remove columns by right-clicking on any of the column headers.