On this page, we discuss various networking strategies and explain how to run a digital signage network on top of an existing network. Broadsign Control helps secure any digital signage network with features that include user-level access privileges, data encryption, and file integrity checking.
SOC 2 Type 2
Broadsign successfully completed the Service Organization Control (SOC) 2 Type 2 audit. This audit sets standards for security, availability, process integrity, confidentiality, and privacy for SaaS and cloud-based companies. As digital signage network operators increasingly leverage cloud services to store data, compliance ensures that service providers follow strict security policies and procedures to protect the integrity and confidentiality of their clients’ data.
Building on our original SOC 2 Type 1 certification, SOC 2 Type 2 is a more rigorous audit that evaluates the execution of an organization’s security program over a period of time. As a result, our successfully completed SOC 2 Type 2 audit is a more in depth review of the ongoing state of our cloud security.
SOC 2 compliance provides added trust and assurance to protect Broadsign customers’ data in the cloud. Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 evaluates the internal systems and security controls a tech service business uses to protect customer data in the cloud. As digital threats continue to evolve and cybersecurity remains a top business challenge, SOC compliance has become a gold standard to ensure organizations are adhering to best practices when securing sensitive internal and customer data. Having a SOC 2 report is a badge of trust and an important step in providing our customers with added peace of mind.
Security in the digital signage industry is important, especially given the public nature of the screens and the prominence of cloud-based services. In a recent survey conducted by Broadsign, security and reliability ranked amongst the top three concerns that digital signage media owners have for their networks.
The following image illustrates the standard network layout used by the majority of Broadsign clients.
Site with One Player PC
In a site with one player PC, each requires an outbound connection to the public Internet on port 443.
Broadsign Control Edge Server Scenario
In a Broadsign Control Edge Server scenario, the edge server downloads content from the main server once and redistributes it quickly over the LAN to save bandwidth using TCP port 10805. An outbound connection on port 10799 for scheduling and reporting traffic is also required. Player PCs connected to an edge server for content need an outbound connection to the public internet on port 443 for scheduling and reporting information, whereas all content will be acquired from the edge server on the local LAN over port 10805. No inbound ports need to be opened in either case.
- Port 10805 is used for Content Transfer Protocol (CTP).
- Port 10799 is used for Digital Signage Control Protocol (DSCP).
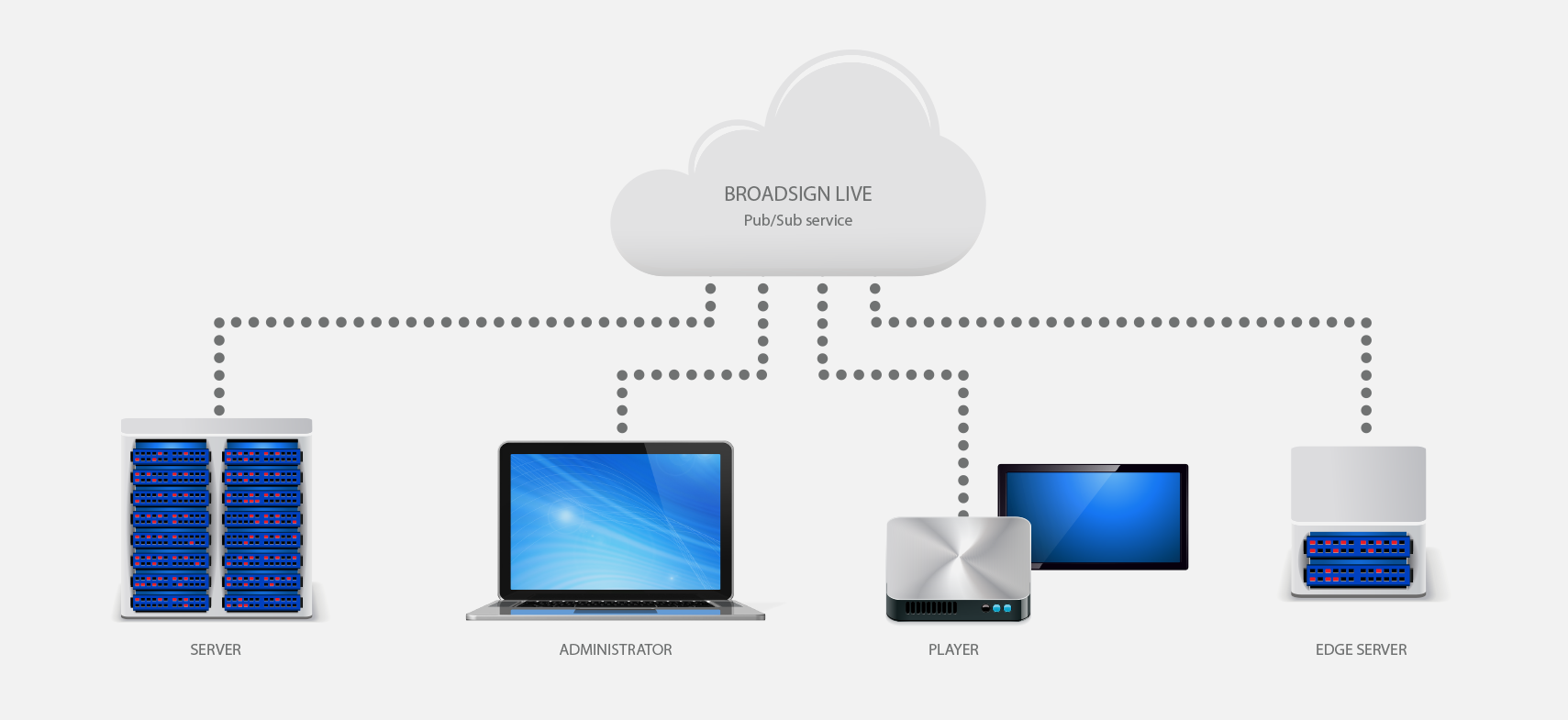
Broadsign Control Live Enabled
In a scenario where Broadsign Control Live is enabled, the Player connects to an additional service (Cloud-based Pub/Sub service) via an HTTPS and/or websocket request on outbound port 443. The Broadsign Server also connects to that channel. When a user in Broadsign Control Administrator clicks "poll now" or "request screenshot", the instructions go as follows:
- From Broadsign Control Administrator to Broadsign Server
- From Broadsign Server to the cloud-based Pub/Sub service
- From the cloud-based Pub/Sub service down to the Player.
The Player only receives commands via this channel, not full payloads, so for example, the "poll now" command coming down through the cloud-based service just tells the Player to initiate an immediate poll via normal polling channels (port 443).
Broadsign Control Player
Broadsign Control Player uses port 443 to direct its traffic to the main server housed in Montreal, Canada. Any global digital signage network operator can use this data centre as the application is not at all sensitive to latency, and Montreal is well-connected to all global links.
Port 443 is used for polling the server at defined intervals for exchanging control information and data with the server. Broadsign Control Player needs to connect back to the main server through the internet over this port to receive its latest scheduling information, configurations and report any cached incidents and proof of play data. The amount of information exchanged per day varies based on many parameters, but will typically be in the range of 2-5 MB per day.
Port 443 is also used for delivering ad copies (content files such as videos, images, HTML5, etc). Content files can come either from the main Montreal server or a Broadsign Control Edge Server used as a content cache server. A player will always prefer the local cache but can fall back to the main server when needed.
Broadsign Control Player uses port 10799 only in the case of self-registration, as described in Register a Player. Port 10799 is the TCP port used for polling the server at defined intervals for exchanging control information and data with the server.
Broadsign Control Edge Server
As mentioned above, the Broadsign Control Edge Server can save bandwidth at sites with multiple player PCs that need the same content. A hierarchy of edge servers can also be developed to reduce bandwidth requirements when pushing out large files.
Ports 10799 and 10805 must be open for outbound traffic to the Internet. For security reasons, Broadsign Server will never try to initiate an inbound connection into a network. Instead, Broadsign Control Player initiates communication to the server using either port.
Note: For more details of the network parameters required for integration with Broadsign Control, see Network Access Rules.
Outbound access to port 80 might be required to enable certain scenarios such as HTML5 content loading assets dynamically over HTTP/HTTPS, Broadsign Publish, and automated crash dump reporting.
Outbound access to port 21, destined to pickup.broadsign.com will allow Broadsign support to collect remote diagnostics about players to troubleshoot certain types of issues.
Note: For more details of the network parameters required for integration with Broadsign Control, see Network Access Rules.
You can configure Broadsign Control Player to use an HTTP or SOCKS 5 proxy server through which all connections tunnel. This can be useful in bypassing situations where the client network refuses outbound traffic on the required ports.
For more information, see Options under the "hamburger" icon of the Broadsign Control Player interface.
Using Broadsign’s network control feature, specific times for the playback PC to use the network are designated to limit Broadsign Control Player from consuming a site’s bandwidth.
For example, Broadsign Control Player can only download large content files at night while allowing polling service to continue throughout the day. This conservation tactic would be useful at a store using POS debit and credit card bandwidth, as the bandwidth required for polling data is much less than content downloads and does not interfere with local network availability.
For more information, see Network Control.
All applications within the Broadsign platform are equipped with TLS v1.X (Transport Layer Security) functionality.
Broadsign uses OpenSSL as its TLS implementation.
File integrity verification is important in the detection of tampered or corrupt media files and prevention of their distribution throughout the network. Broadsign Control verifies file integrity by calculating a checksum on every media file imported into the system. A checksum is a mathematical formula that derives a large number from a file in a way that is very difficult to reproduce. Broadsign uses a checksum implementation that is both secure and computationally efficient.
Broadsign Control Player
Before a file can play, file integrity must be ensured. Once all pieces have been verified, a checksum is computed on the file before it can be used.
Broadsign Control Edge Server
Before a file can play, three levels of file integrity are ensured:
- As mentioned above, the CTP2 protocol ensures that each file is broken into pieces of approx 1-5 MB, and each piece is broken into blocks of 64 KB. Each block has a checksum that must pass before it is used.
- Each piece has an extra checksum once it has accumulated all the valid blocks within it.
- Once all pieces have been verified, the file is reconstructed with all the pieces and a final checksum is computed before it can be used.
Dedicated Mode
Broadsign Control Player, installed and required on all playback PCs for the display of scheduled content, runs in dedicated mode to prevent access to the playback PC’s file system. This dedicated mode is far superior to just allowing an autostart user with a default startup program.
The dedicated mode provides a custom application shell which executes the player in a sandboxed environment with very restricted access to the underlying OS.
Broadsign Control Player starts automatically in this restricted shell as a restricted user without requiring that any privileged user is logged in. As such, if a user connects locally or remotely and tries to interrupt the running of the Broadsign Control Player software, the user will be faced with the login screen requiring a password to prevent unauthorized local file structure access.
For more information about dedicated mode on Windows, see Install the Player on Windows.
For more information about dedicated mode on Ubuntu Linux, see Step 5: Dedicate Broadsign Control Player on Linux.
Broadsign Control enforces its role-based security policy at two levels:
- the local application level
- the remote server level
Broadsign Server mediates access to a database shared by all agents in the network by providing an interface to execute operations and queries. Since all operations and queries on the database must be performed through this interface, Broadsign Server controls how the database is accessed. Furthermore, Broadsign Server enforces permission checks for each element of its interface using the currently logged-in user’s role(s). Access-level verification is performed for every command executed on Broadsign Server - this is the true way to guarantee access control lists are enforced.
Broadsign Control Administrator also changes its appearance based on privileges of the logged-in user, so that resources the user does not have access to can’t be viewed and actions are disabled so they cannot be used. Local permission checks in Broadsign Control Administrator can be exploited but Broadsign Server is the gatekeeper and operations to which the user does not have access will fail.
For more information, see Users and Add Users and User Groups.
Broadsign used to operate a cluster for its SaaS service based out of a carrier-grade third-party data center in Montreal. In a move to increase the quality and security of our data center, Broadsign now operates a cluster for its SaaS service based out of the Cloud provider AWS (Amazon Web Services).
The AWS Global Cloud Infrastructure is the most secure, extensive, and reliable Cloud Computing environment anywhere.
The key features of this data center are available in the AWS Global Cloud Infrastructure page.